Management of Critical Chain Projects (CCPM)
Dr. Eliyahu M. Goldratt developed and popularized Critical Chain Project Management in 1997. Followers of this Project Management methodology claim it is an alternative to the established standard of Project Management as advocated by PMBOK® and other Project Management standards. In this article, we will provide a brief overview of the Critical Chain Project Management principles and their applicability to project management across all organizations and verticals.
The Critical Chain Method derives from another of Dr. Goldratt’s innovations: the Theory of Constraints (TOC). This project management method takes effect after the initial project schedule, which includes establishing task dependencies, is completed. The Critical Chain Method is used to rework the evolved critical path. To accomplish this, the methodology takes into account the constraints associated with each task.
Among these constraints are:
Each task contains some degree of uncertainty.
Team members or task owners frequently overestimate task durations. This is typically done to add a safety margin to the task in order to ensure that it is completed within the time frame specified.
In most cases, the tasks should be completed sooner rather than later, even if the time estimate includes a safety margin.
If the assumed safety margin is not required, it is wasted. If the task is completed sooner, it does not always mean that the successor task can begin sooner because the resources needed for the successor task may not be available until their scheduled time. In other words, the time saved cannot be used to complete the project earlier. If, on the other hand, there are delays that exceed the estimated schedules, these delays will almost certainly be passed on and, in most cases, will exponentially increase the project schedule.
With the assumptions stated above, the Critical Path Methodology of project management suggests pooling task buffers and adding them at the end of the critical path:
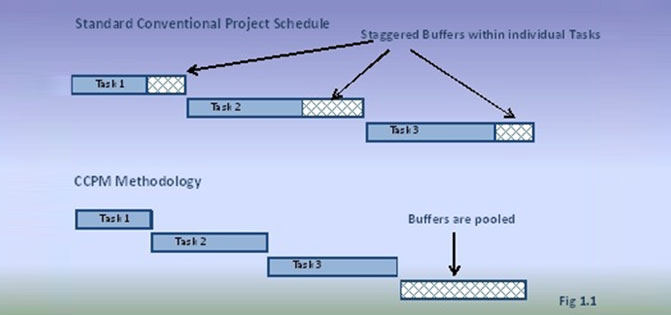
The Critical Path Buffers are classified into three types by project management.
Buffer for Projects
The project buffer is the total pooled buffer depicted in the image above.
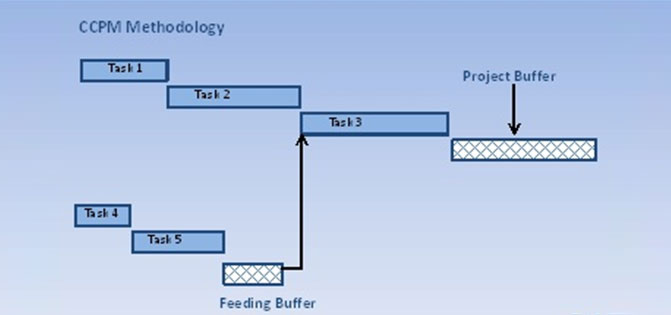
Buffering Feeding
There are path/s in a project network that feed into the critical path. The pooled buffer on each such path represents the feeding buffer to the critical path (shown below), providing some slack to the critical path.
Buffer of Resources
This is a virtual task that is inserted immediately before critical chain tasks that require critical resources. This serves as a trigger point for the resource, signaling the start of the critical path.
The critical chain is recalculated as the project’s progress is reported. In fact, the project’s monitoring and control were primarily focused on buffer utilization. As you can see, the critical chain method takes the basic critical path-based project network and schedule into account to generate a completely new schedule.
In organizations that lack advanced project management practices, the critical path project management methodology is extremely effective.
However, the methodology discourages multitasking, and in projects with complex schedule networks, the results of implementing the critical path methodology have proven to be a detriment to the overall project schedule. Furthermore, there is no standardized method for calculating and optimizing project buffers. The critical path project management methodology has had some success in the manufacturing industry; however, it has had no notable success in the IT industry.
Similarly, the project management event chain methodology focuses on determining the uncertain events and the chain reactions they cause. It is an uncertainty modeling method that is based on Monte Carlo analysis, Bayesian Belief Networks, and other well-established simulation methodologies. When events occur, they can trigger other events, resulting in an event chain that can effectively change the course of the project. Events and event chains are identified, and quantitative analysis is carried out to determine the extent of the uncertainty and its likely impact on the project. This exercise yields critical event chains, which have the potential to have a significant impact on the project. Event chain diagrams are visual representations of events, event chains, and the consequences of those events.

It is obvious that neither the critical path project management methodology nor the event chain methodology can be regarded as alternatives to the standard project management methodology advocated by PMBOK. While the critical path project management methodology is best used for deriving project schedule networks, the event chain project management methodology can be used for quantitative risk analysis.
Conclusion
SPOTO Learning offers a variety of project management courses that will help you pass your PMP® or PRINCE2® exam, including the PRINCE2 Foundation Certification Training Course and the PMP Certification Training Course. Our PMP training courses are led by certified, highly experienced professionals with a minimum of ten years of experience.





